Table of Contents
In Laravel websites, encryption and decryption are essential for protecting sensitive data like user credentials and personal information. Laravel’s default encryption system uses secure algorithms to safeguard this data, ensuring it stays confidential. However, in some cases, you may need to use a custom key for specific scenarios.
In this blog, we’ll dive into what encryption and decryption are, how Laravel handles them, and the benefits of using Laravel’s built-in system. We’ll also show you how to encrypt and decrypt data using a custom key. Additionally we’ll also learn the best practices you can follow to ensure security.
What is Encryption and Decryption in Laravel?
Encryption is the process of converting plain text data into a coded format that is cryptic to unauthorized parties. Decryption is the reverse process of converting encrypted data back into its original plain text form. This ensures that sensitive data remains protected during storage and only authorized parties can read it by decrypting the information.
Laravel provides a built-in encryption system that uses AES-256 and AES-128 encryption algorithms. That ensures strong security. These algorithms are symmetrical, meaning the same key is used for both encryption and decryption processes. The framework simplifies encryption by offering built-in methods to securely encrypt and decrypt data using its Crypt facade.
Here’s a brief overview of the encryption and decryption in Laravel:
Encryption
Encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext). This prevents unauthorized access to sensitive information. Here is a example code for encryption:
use Illuminate\Support\Facades\Crypt;
$encrypted = Crypt::encrypt('This is a secret message.');
In the above example, ‘This is a secret message.’ is encrypted and can’t be understood by anyone who doesn’t have the key.
Decryption
Decryption is the reverse process of encryption. Here, the unreadable ciphertext is converted back into its original readable form (plaintext) using the same key. Here is an example where we’ll use the decrypt() method for decrypting message:
$decrypted = Crypt::decrypt($encrypted);
The above code decrypts the previously encrypted string back to its original form: ‘This is a secret message.’.
How Laravel Handles Encryption and Decryption?
Laravel provides a seamless way to encrypt and decrypt sensitive data using the Crypt facade. This encryption is powered by OpenSSL, a widely used cryptographic library. Plus, Laravel implements the AES-256-CBC encryption algorithm by default. Below is a detailed look at how Laravel manages encryption and decryption:
Stage 1: Laravel’s Encryption Algorithm
Laravel uses symmetric encryption, meaning the same key is used for both encrypting and decrypting data. By default, Laravel’s encryption system leverages the AES-256 or AES-128 encryption algorithms. These algorithms require a key to lock (encrypt) and unlock (decrypt) the data.
Laravel stores the encryption key in the .env file under the key APP_KEY. This key is automatically generated when you set up a Laravel project and is required for both encryption and decryption.
Here is an example of .env file:
APP_KEY=base64:randomgeneratedkeyhere==
This key ensures that encrypted data can only be decrypted by the same application instance or another instance that has the exact same key.
Stage 2: The Crypt Facade
Laravel provides a simple Crypt facade to handle encryption and decryption, abstracting away the complexity of cryptographic operations. The Crypt facade comes with two main methods:
- encrypt(): Encrypts data.
- decrypt(): Decrypts previously encrypted data.
Using both of these crypt methods Laravel can handle the encryption and decryption of data.
Stage 3: Encryption Process
When encrypting data, Laravel generates a secure ciphertext using several components to ensure safety:
- Initialization Vector (IV): Laravel generates a random initialization vector (IV) for each encryption operation. The IV ensures that encrypting the same data multiple times produces different encrypted results, enhancing security.
- CBC Mode: Laravel uses CBC (Cipher Block Chaining) mode for AES encryption. CBC mode increases the security of encrypted data by making each block of plaintext dependent on the previous one.
- Message Authentication Code (MAC): Laravel attaches a MAC (Message Authentication Code) to the encrypted data to ensure its integrity. The MAC prevents attackers from tampering with the encrypted data, as any modification would invalidate the MAC during decryption.
Example of encrypted data (Base64 Encode):
eyJpdiI6IlZkSVhzOTFkVGVJN3h3RWxFIiwibm9uY2UiOiJkUHVna3NkZWpLdTFhUnBlVUpBcm93IiwidGFnIjoidGVzdCJ9
This is a base64-encoded string, which contains: IV (Initialization Vector), encrypted data (ciphertext), and the MAC (Message Authentication Code).
Stage 4: Decryption Process
When decrypting data, Laravel performs the following steps:
- Extracting the IV, Ciphertext, and MAC: Laravel extracts the IV, ciphertext, and MAC from the encrypted string.
- Validating the MAC: The MAC is checked to ensure that the encrypted data has not been tampered with. If the MAC validation fails, Laravel throws a DecryptException, indicating that the decryption was unsuccessful due to invalid or altered data.
- Decrypting the Ciphertext: If the MAC is valid, Laravel uses the stored APP_KEY and the extracted IV to decrypt the ciphertext, converting it back to its original plaintext form.
Here is the example code of how decryption is handled:
use Illuminate\Support\Facades\Crypt;
try {
$decrypted = Crypt::decrypt($encrypted);
} catch (Illuminate\Contracts\Encryption\DecryptException $e) {
// Handle the decryption failure
echo "Decryption failed!";
}
In this example, if the decryption process fails, Laravel will throw an exception that you can handle by showing an error message.
Stage 5: Key Management and Security
Laravel’s encryption system heavily relies on the security of the encryption key (APP_KEY). Some important points for key management are as follows:
- Storing Keys in .env: Laravel recommends storing the encryption key in the .env file for better security. This prevents hardcoding keys directly in code, which could pose a security risk if the codebase is shared.
- Generating a Key: You can generate a secure encryption key using Laravel’s built-in command:
php artisan key:generate
- Key Rotation: If you need to rotate your encryption key (for example, for security compliance), Laravel provides ways to handle key rotation. However, be aware that rotating keys will require re-encrypting existing data, as previously encrypted data cannot be decrypted with a new key.
Laravel’s encryption system makes it easy to safeguard sensitive data with AES-256 encryption. However, managing the APP_KEY carefully and ensuring it is not exposed is crucial for maintaining data integrity and security. Similarly, applying validation rules like Laravel Unique helps maintain data accuracy and consistency within your application.
If you are looking to build a site that is secure and robust consider getting service from expert Laravel development company.
How to Encrypt and Decrypt with a Custom Key in Laravel?
To encrypt and decrypt data with a custom key in Laravel, you can utilize Laravel’s built-in encryption capabilities by slightly modifying them. Below are the essential steps:
Step 1: Install Laravel
Before starting the encryption and decryption process, make sure you have a Laravel project set up. If you don’t have one, follow these steps to create your Laravel project:
First, install Laravel globally via Composer using the command:
composer global require laravel/installer
Next, create a new Laravel project with the name of your choice:
laravel new my-laravel-app
After that navigate to your Laravel project directory:
cd my-laravel-app
Step 2: Generate a Custom Encryption Key
Laravel uses an encryption key to encrypt and decrypt data. Typically, this key is stored in the .env file under APP_KEY. To encrypt data with a custom key, you need to define your custom key. You can generate a custom key using Laravel’s built-in helper:
php artisan key:generate --show
This will output a key that looks something like:
base64:VGhpcyBpcyBteSBjdXN0b20gZW5jcnlwdGlvbiBrZXk=
Now store the key in a safe place (e.g., environment file or a secure database). Ensure it’s base64-encoded. If it’s not, manually encode it:
$key = base64_encode(random_bytes(32));
Step 3: Create Encryption and Decryption Helper Functions
Laravel’s built-in encryption system (Crypt facade) uses the application key by default. To use a custom key, you’ll need to modify the default behavior.
First, create a custom encryption function you want to implement:
use Illuminate\Support\Facades\Crypt;
use Illuminate\Contracts\Encryption\DecryptException;
use Illuminate\Encryption\Encrypter;
function customEncrypt($data, $customKey) {
$key = base64_decode($customKey);
$encrypter = new Encrypter($key, config('app.cipher')); // Cipher: AES-256-CBC by default
return $encrypter->encrypt($data);
}
Explanation:
- base64_decode($customKey): Decodes the custom key, as Laravel expects the key in binary form.
- Encrypter($key, config(‘app.cipher’)): Instantiates a new encryption class using the custom key.
- encrypt($data): Encrypts the provided data.
Now create a custom decryption function. Here is an example code:
function customDecrypt($encryptedData, $customKey) {
try {
$key = base64_decode($customKey);
$encrypter = new Encrypter($key, config('app.cipher'));
return $encrypter->decrypt($encryptedData);
} catch (DecryptException $e) {
// Handle the exception
return 'Decryption failed: ' . $e->getMessage();
}
}
Explanation:
- decrypt($encryptedData): Decrypts the encrypted data using the custom key.
- DecryptException: Catches any issues that might occur during decryption.
Step 4: Define the Encryption Cipher
Laravel supports two types of encryption ciphers: AES-128-CBC and AES-256-CBC. By default, Laravel uses AES-256-CBC, which is secure and recommended. You can confirm or change the cipher in the config/app.php file:
'cipher' => 'AES-256-CBC',
If you want to use a different cipher (e.g., AES-128-CBC), update this value accordingly.
Step 5: Test the Encryption and Decryption
You can now test the encryption and decryption functions. Use any controller, route, or artisan command to encrypt and decrypt data. For example, in a route:
use Illuminate\Support\Facades\Route;
Route::get('/encrypt', function () {
$customKey = 'base64:VGhpcyBpcyBteSBjdXN0b20gZW5jcnlwdGlvbiBrZXk=';
$data = 'This is a secret message';
// Encrypt the data
$encrypted = customEncrypt($data, $customKey);
return "Encrypted data: $encrypted";
});
Route::get('/decrypt', function () {
$customKey = 'base64:VGhpcyBpcyBteSBjdXN0b20gZW5jcnlwdGlvbiBrZXk=';
$encrypted = 'Your encrypted string here';
// Decrypt the data
$decrypted = customDecrypt($encrypted, $customKey);
return "Decrypted data: $decrypted";
});
Step 6: Secure Your Custom Key
It’s crucial to keep the encryption key secure. Here are some tips:
- Store your custom key in a secure location, such as a vault or environment variable (.env file).
- Avoid hardcoding sensitive keys directly in the codebase.
- Use proper access control to ensure that only authorized users can access the encryption key.
Step 7: Handle Exceptions
When dealing with encryption and decryption, it’s important to handle exceptions (like when decryption fails due to a wrong key or tampered data). Laravel’s DecryptException should be caught to ensure your application doesn’t crash:
try {
$decrypted = customDecrypt($encrypted, $customKey);
} catch (DecryptException $e) {
return 'Decryption failed: ' . $e->getMessage();
}
With that, we have successfully implemented encrypt and decrypt using a custom key in Laravel. Now let’s understand what are the benefits you can have by using a custom key for encryption and decryption in Laravel.
Why Encrypt and Decrypt With a Custom Key in Laravel?
In Laravel, the built-in encryption system uses the APP_KEY stored in the .env file for all encryption and decryption operations. However, there are scenarios where using a custom key for encryption and decryption becomes necessary. Here’s why you might want to use a custom key for encryption in Laravel:
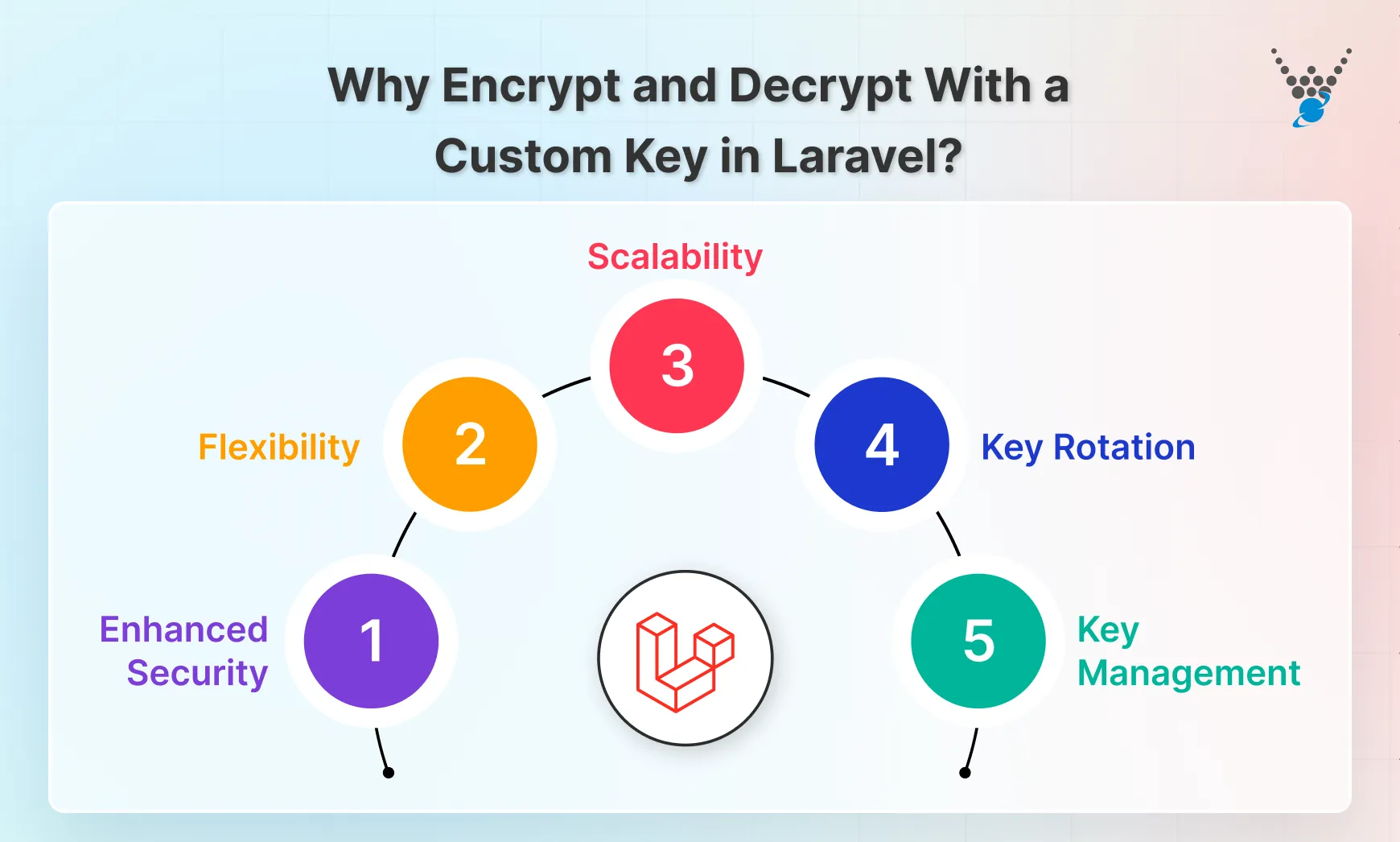
Enhanced Security
Using a custom encryption key can significantly enhance the security of your application. By using a separate key for sensitive data, you add an additional layer of protection. If the default APP_KEY is compromised, the custom key ensures that not all encrypted data is immediately at risk. This thereby reduces the potential impact of a security breach.
Flexibility
A custom encryption key offers more flexibility in terms of encryption algorithms and ciphers. You can choose an algorithm that better suits your specific requirements or integrates with external systems. This flexibility allows you to customize the encryption process to your application’s unique needs.
Scalability
A custom key allows you to easily manage encryption keys across different environments (e.g., development, staging, production) without affecting the security of your data. You can also implement regular key rotation to further enhance security and reduce risks associated with long-term key usage.
Key Rotation
Regularly rotating the encryption key is a crucial security measure that can help reduce the risk of unauthorized access. By using a custom key, you can implement a key rotation policy that aligns with your organization’s security best practices. Key rotation can also help meet compliance requirements that mandate regular key changes.
Key Management
A custom encryption key allows you to implement centralized key management practices. That can ensure the key is stored and managed securely. By using a dedicated key management system, you can reduce the risk of unauthorized access and maintain control over the key throughout its lifecycle.
These benefits of using custom encryption keys in Laravel provides several benefits including enhanced security and scalability.
Best Practices for Encryption and Decryption in Laravel
When working with encryption and decryption in Laravel, following these best practices can significantly enhance the security and compliance of your website. Along with data protection, implementing tools like Laravel cookie consent ensures transparency and adherence to privacy regulations.
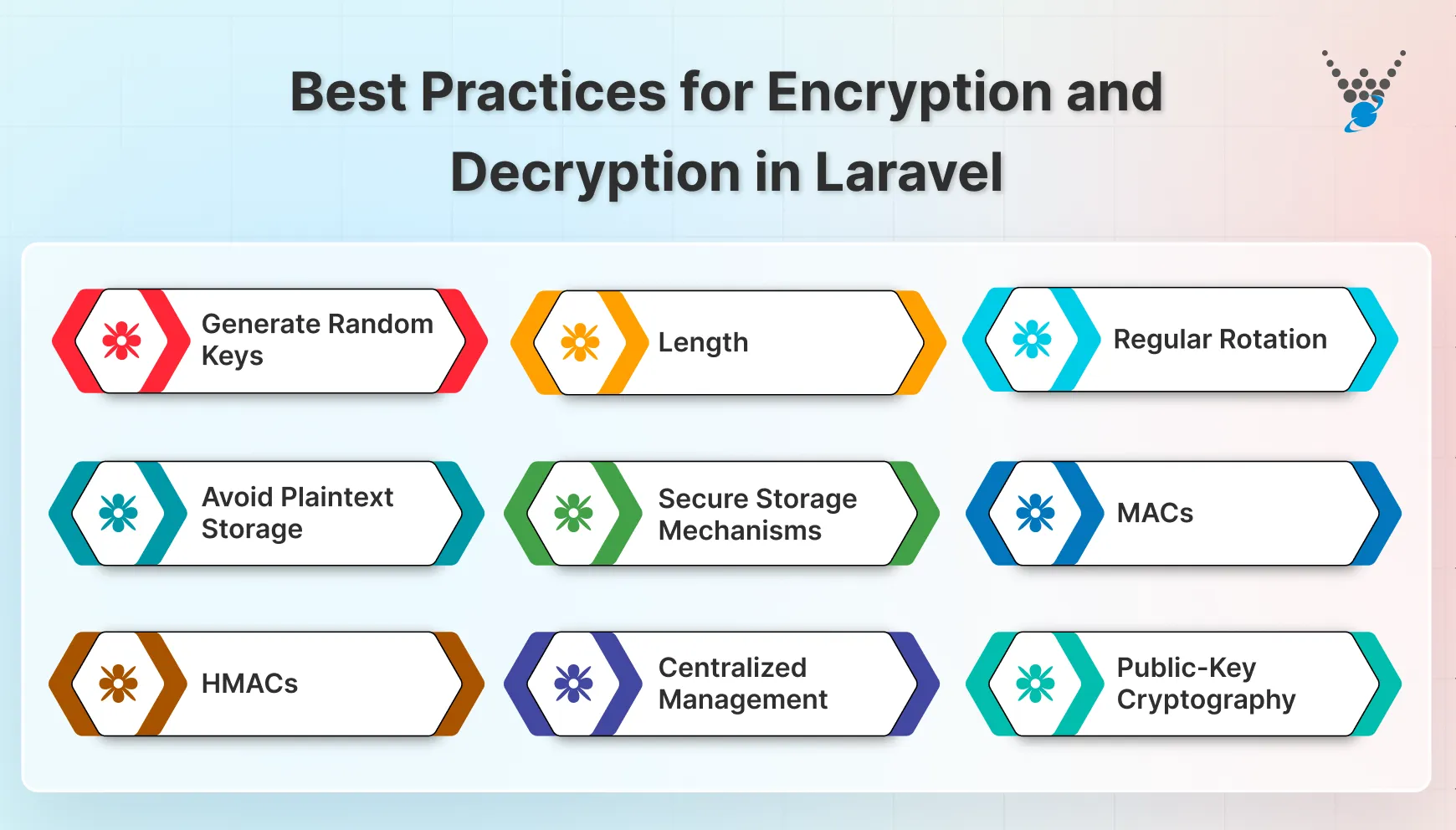
- Generate Random Keys: Use a cryptographically secure random number generator (CSPRNG) to create strong encryption keys.
- Length: Ensure keys are sufficiently long. At least 256 bits is recommended for most websites.
- Regular Rotation: Periodically rotate encryption keys to reduce the risk of compromise.
- Avoid Plaintext Storage: Never store encryption keys in plain text within your codebase or configuration files.
- Secure Storage Mechanisms: Consider using environment variables, secrets management services, or secure key vaults to store keys.
- MACs: Use Message Authentication Codes (MACs) to verify the integrity of encrypted data and protect against tampering.
- HMACs: HMACs are a type of MAC that combine a cryptographic hash function with a secret key.
- Centralized Management: Implement a centralized system to manage encryption keys, including generation, rotation, and storage.
- Public-Key Cryptography: For scenarios requiring key exchange or digital signatures, consider using asymmetric encryption algorithms like RSA (Rivest Shamir Adlemanor) ECC (Elliptic Curve Cryptography).
By following these best practices, you can significantly enhance the security of your Laravel website. If you want to build a website with the best security practices followed, hire dedicated Laravel developers.
Wrapping Up
Encryption and decryption play a vital role in ensuring sensitive information remains safe from unauthorized access. Laravel’s default encryption, powered by AES-256-CBC and tied to the APP_KEY, provides robust protection. However, using a custom encryption key offers additional flexibility, enabling you to manage multiple keys and enhance security.
By understanding the core concept of encryption and decryption you can understand the basics of implementing them. To encrypt and decrypt data with a custom key in Laravel you can define the custom encryption and decryption function. Once done, you can follow best practices and handle exceptions with DecryptException.If you are struggling to build a website that is secure and performs optimally, contact us now.
FAQs About Laravel Encrypt and Decrypt
How can I decrypt data in Laravel?
Use the ecrypt() function or Crypt::decryptString() to decrypt the encrypted value. Make sure the encryption key hasn’t changed since encryption.
What encryption algorithm does Laravel use?
By default, Laravel uses AES-256-CBC and AES-128-CBC for encryption. These algorithms are known for their strong security and efficiency.
How can I use a custom key for encryption in Laravel?
You need to generate a 32-character key (usually base64-encoded) ; you can load it from the environment file (.env). After that you need to initialize Laravel’s Encrypter class with the generated key.
How does Laravel encryption work with user authentication systems?
Laravel encryption enhances the protection of sensitive login credentials and user tokens. When combined with passwordless authentication methods like Laravel Passkeys, it ensures end-to-end security for users without depending solely on passwords.
Build Powerful Laravel Applications
Learn how to leverage Laravel's powerful features for efficient and scalable web development.