Quick Summary
Keeping Laravel applications secure is essential for protecting user data and ensuring reliable projects. This blog covers key risks like SQL injection, XSS, CSRF, and misconfigurations, and offers practical solutions. From HTTPS, authentication, and secure coding to cloud security and CI/CD practices, learn how to build resilient Laravel apps that stay safe, trustworthy, and future-ready.
Table of Contents
If you’re building web apps with Laravel, security should be at the top of your list. Cyber threats are getting sharper every year, and even small gaps in your code can put your users at risk. As developers, we carry the responsibility to protect sensitive data and keep applications safe.
Laravel is a powerful framework, but like any tool, it needs the right care to stay secure. If you follow a few proven practices, you can reduce risks and make your apps stronger against attacks. In this blog, we’ll discuss practical Laravel security best practices that every developer should follow. So, let’s dive in!
What is Laravel?
Laravel is a free, open-source PHP web framework designed to streamline the development process and enhance the overall experience for developers. Created by Taylor Otwell, Laravel follows the MVC (Model-View-Controller) architectural pattern, providing a clean and organized structure for building modern web applications.
- Eloquent ORM: Laravel’s Eloquent ORM simplifies database interactions with an intuitive syntax, allowing developers to perform operations seamlessly, from basic CRUD functions to advanced queries.
- Blade Templating: With Blade, developers enjoy a lightweight yet powerful templating engine, facilitating the creation of dynamic views through features like template inheritance, control structures, and reusable components.
- Artisan Console: Laravel’s Artisan Console automates tasks effortlessly, from generating boilerplate code to handling migrations, enabling developers to focus on writing application-specific logic instead of mundane, repetitive activities.
- Middleware: Using Laravel’s Middleware offers a robust mechanism to filter HTTP requests. So developers can modify, authenticate, or reject requests based on specific conditions, enhancing control over the application’s flow.
- Laravel Mix: Simplifying asset compilation and versioning, Laravel Mix provides a fluent API for defining Webpack build steps. Integrating Laravel Mix is seamless, streamlining the management of CSS, JavaScript, and other assets.
It’s crucial to appreciate the robust foundation that Laravel provides for web development. By understanding the comprehensive set of features that Laravel offers, we can better grasp the importance of safeguarding applications through effective security measures.
Why are Laravel Security Best Practices Important?
As cyber threats continue to grow in sophistication, adopting Laravel security best practices becomes not only a good practice but a critical necessity to safeguard sensitive data and maintain the integrity of your projects.
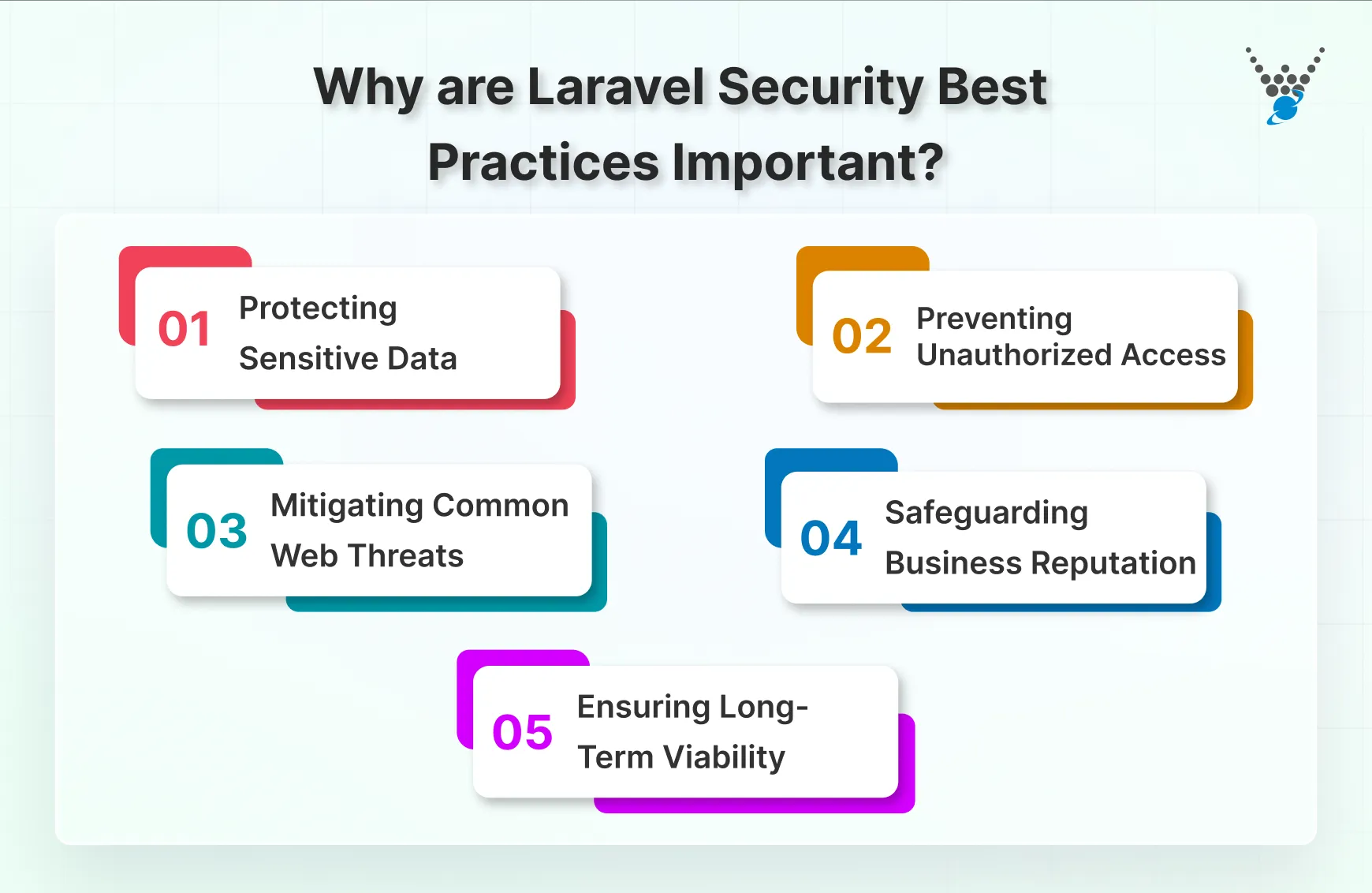
- Protecting Sensitive Data: Implementing security measures in Laravel is essential to shield sensitive user data, including personal information and login credentials, from unauthorized access.
- Preventing Unauthorized Access: Robust security practices in Laravel help prevent unauthorized access to your applications, ensuring that only authenticated users have the appropriate permissions to access sensitive areas.
- Mitigating Common Web Threats: Laravel security best practices are instrumental in mitigating common web threats such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), strengthening your application against potential vulnerabilities.
- Safeguarding Business Reputation: A security breach can significantly damage your business reputation. Adhering to Laravel security best practices not only protects your users but also safeguards the trust and credibility your business has built over time.
- Ensuring Long-Term Viability: Whether you’re embarking on a new Laravel project or securing an existing one, incorporating security practices from the outset ensures the long-term viability of your application, reducing the risk of costly security incidents down the line.
Whether you’re initiating a new project or enhancing the security of an existing Laravel application, collaborating with an experts can be a strategic move.
Common Security Risks in Laravel
Laravel stands as a robust framework, but like any technology, it is not immune to security vulnerabilities. Understanding and mitigating these risks is paramount to ensuring the integrity and confidentiality of your applications. Let’s explore some common security risks in Laravel and strategies to fortify against potential threats.
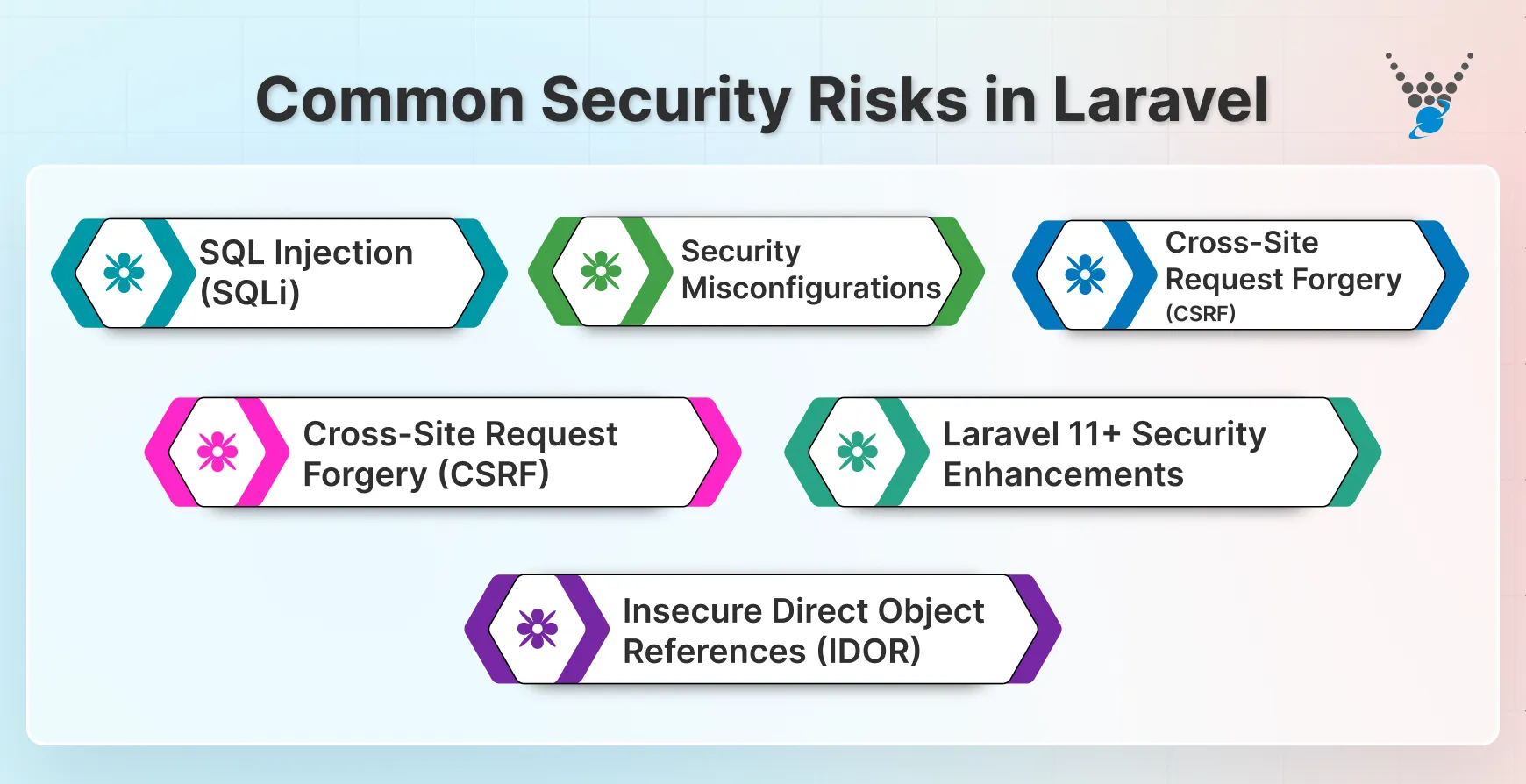
1. SQL Injection (SQLi)
SQL Injection is a common security risk where attackers manipulate user inputs to execute unauthorized SQL queries on a database.
- Use Eloquent ORM: Use Laravel’s Eloquent ORM to interact with the database safely, as it uses prepared statements by default.
- Query Builder: Use Laravel’s Query Builder for secure database queries without concatenating raw inputs.
- Parameterized Queries: Ensure user inputs are treated as data, not executable code, to prevent injection attacks.
- Input Validation: Validate all user inputs to filter out potentially malicious content. You can also use Laravel’s validation rules like Laravel Unique to ensure data integrity and prevent duplicate entries during input validation.
- Database User Permissions: Follow the principle of least privilege, giving each user only the access they need.
This approach, combining Eloquent, Query Builder, parameterized queries, input validation, and proper permissions, significantly reduces SQL injection risks in Laravel applications.
2. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) poses a significant threat to web applications, allowing attackers to inject malicious scripts that can be executed in the browsers of unsuspecting users. In the context of Laravel, a framework that emphasizes secure coding practices, mitigating XSS risks is paramount for maintaining the integrity of user interactions.
- Input Sanitization: Thoroughly sanitize user inputs to strip away potentially harmful scripts, preventing them from being executed in the browser.
- Blade Templating Security: Utilize Laravel’s Blade templating engine to automatically escape output, minimizing the risk of XSS attacks by rendering user-generated content safely.
- Content Security Policy (CSP): Implement and enforce a Content Security Policy to control which sources can be considered trusted for loading content, reducing the risk of unauthorized script execution.
- HTTP-Only Cookies: Set cookies as HTTP-only to prevent client-side scripts from accessing sensitive cookie information, enhancing overall session security.
- Regular Security Audits: Conduct regular security audits of your Laravel application’s codebase to identify and address potential XSS vulnerabilities promptly.
By adopting a robust strategy encompassing input sanitization, Blade templating security, Content Security Policy implementation, and routine security audits, Laravel developers can fortify their applications against the pervasive threat of Cross-Site Scripting.
3. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) stands as a threat where an attacker can exploit the trust a user has in a website to perform unauthorized actions without their knowledge. For Laravel developers, addressing CSRF risks is fundamental to maintaining the integrity of user interactions and safeguarding sensitive actions within applications.
- CSRF Tokens: Laravel provides built-in protection through CSRF tokens. Ensure these tokens are implemented in forms to validate the origin of requests and thwart unauthorized actions.
- SameSite Cookie Attribute: Leverage the SameSite attribute for cookies to restrict their scope, reducing the risk of CSRF attacks by preventing cross-origin requests from sending user credentials.
- Custom Middleware: Implement custom middleware to verify the presence and validity of CSRF tokens on sensitive routes, adding an extra layer of protection.
- Encrypted Request Parameters: Encrypt sensitive request parameters to enhance security, making it more challenging for attackers to manipulate or forge requests.
- User-Friendly Feedback: Provide clear and concise feedback to users regarding successful or failed actions, enhancing transparency and helping users identify any suspicious activity.
As web security remains a critical concern, Laravel developers must prioritize addressing CSRF risks to fortify their applications against unauthorized actions. This proactive approach not only aligns with Laravel’s commitment to security but also contributes to a safer online environment for users.
4. Insecure Direct Object References (IDOR)
It represents a vulnerability where an attacker can gain unauthorized access to objects or data by manipulating input parameters. Laravel developers must address IDOR risks to uphold data confidentiality and protect against unauthorized data access.
- Strict Access Controls: Implement and enforce strict access controls to ensure that users can only access data and resources for which they have explicit authorization.
- Data Validation: Thoroughly validate and sanitize user inputs to prevent the manipulation of input parameters that could lead to unauthorized data access.
- Use Resource IDs: Avoid using direct references or predictable identifiers in URLs, opting instead for resource IDs that are harder for attackers to predict or manipulate.
- Role-Based Access Control (RBAC): Implement RBAC to assign specific roles and permissions to users, limiting their access to only the resources necessary for their tasks.
- Logging and Monitoring: Implement comprehensive logging and monitoring mechanisms to detect and respond to any suspicious or unauthorized access attempts.
Addressing Insecure Direct Object References (IDOR) is imperative for Laravel developers aiming to fortify their applications against unauthorized data access. This proactive approach aligns with Laravel’s commitment to security, ensuring the confidentiality and integrity of sensitive data within applications.
5. Security Misconfigurations
security misconfigurations represent a common vulnerability, stemming from incorrectly configured settings, permissions, or dependencies. You must address security misconfigurations diligently to prevent potential exploits and ensure the overall robustness of their applications.
- Regular Configuration Audits: Conduct regular audits of your Laravel application’s configurations to identify and rectify any misconfigurations promptly.
- Least Privilege Principle: Adhere to the principle of least privilege by restricting user and system permissions to the minimum necessary for proper functionality, reducing the attack surface.
- Update Dependencies: Stay vigilant about updating and patching dependencies to mitigate known vulnerabilities and ensure compatibility with the latest security features.
- Error Handling Practices: Implement proper error handling practices to avoid exposing sensitive information in error messages, preventing potential security risks.
- Secure File and Directory Permissions: Configure file and directory permissions with precision, ensuring that only authorized users or processes have the necessary access.
Mitigating security misconfigurations is crucial for Laravel developers. Through regular audits, adherence to the least privilege principle, dependency updates, error handling, and secure file permissions, a robust defense aligns with Laravel’s commitment to security.
6. Laravel 11+ Security Enhancements
Laravel 11 introduces several security enhancements to bolster application defenses:
- Secure-by-Default Middleware Stack: New applications now come with a pre-configured set of security middleware, including CSRF protection, session encryption, and cookie security, reducing the risk of common vulnerabilities.
- Graceful Encryption Key Rotation: Enables the seamless rotation of encryption keys without disrupting active user sessions, thereby enhancing Laravel’s data protection.
- Per-Second Rate Limiting: Provides more granular control over request throttling, aiding in the prevention of brute-force attacks.
- Enhanced Security Headers: Automatic inclusion of HTTP security headers like HSTS, CSP, and X-Content-Type-Options to mitigate XSS and other attacks.
- Improved CSRF Protection: Enhanced token handling to reduce the chances of token reuse or tampering, strengthening session security.
These enhancements provide Laravel developers with robust tools to secure Laravel applications against evolving security threats.
By staying aware of these risks and leveraging Laravel’s built-in protections and new security enhancements, developers can build secure and reliable applications.
Laravel Security Best Practices
Enhancing security in Laravel is a paramount concern. By adopting a proactive approach and implementing key security measures, you can fortify your applications against potential threats, ensuring the integrity and confidentiality of user data. Let’s explore actionable steps to elevate the security posture of Laravel projects and create a robust defense against common vulnerabilities.
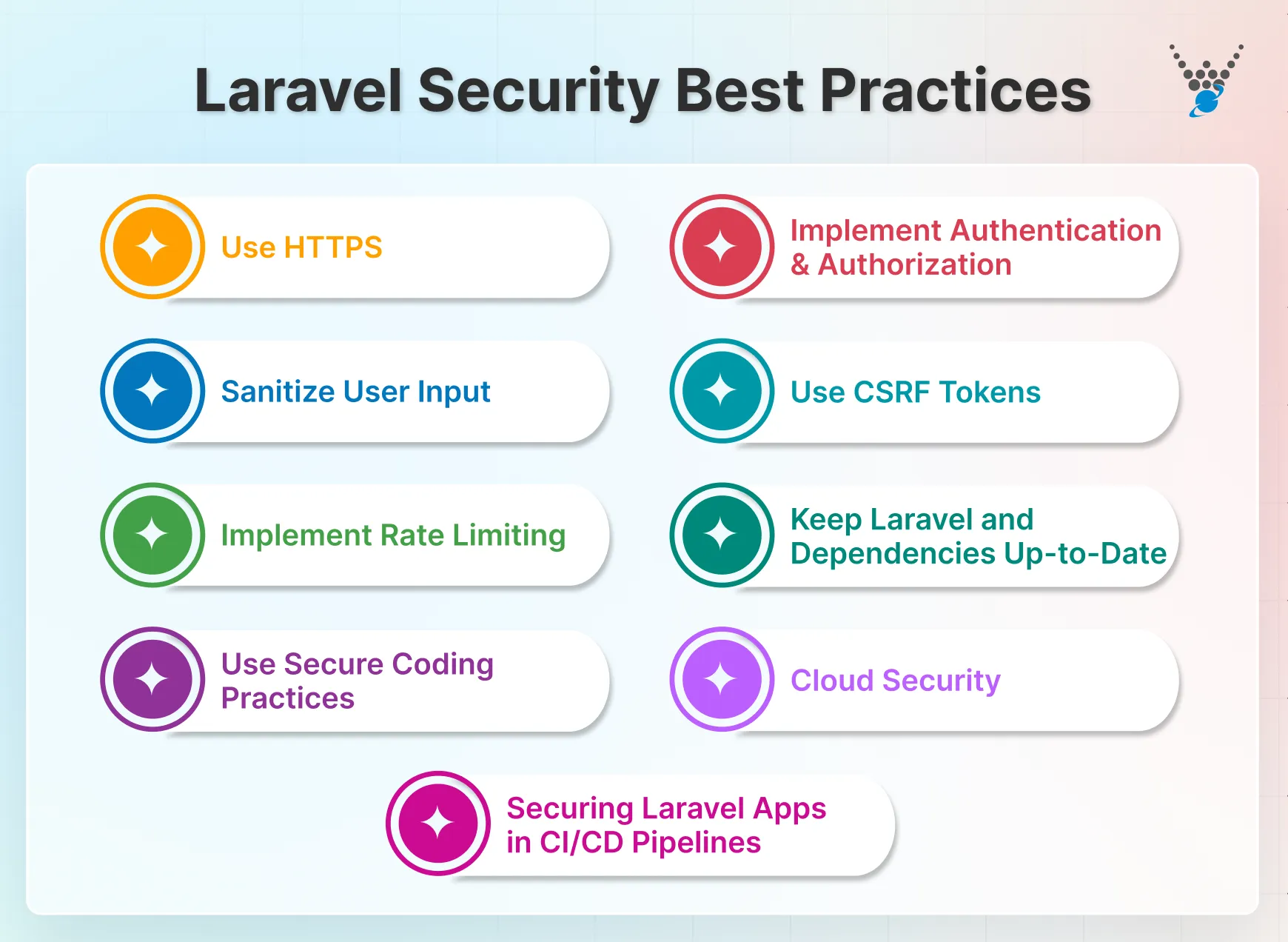
1. Use HTTPS
Adopting HTTPS is a fundamental practice that safeguards data transmission between users and web servers. As an essential step in improving the security of your Laravel applications, the implementation of HTTPS offers encryption and authentication, mitigating the risk of various cyber threats.
- Data Encryption: HTTPS encrypts data in transit, preventing eavesdropping and safeguarding sensitive information exchanged between users and the server.
- User Authentication: HTTPS ensures the authenticity of your website, assuring users that they are interacting with a legitimate and secure platform.
- SEO Benefits: Search engines prioritize secure websites, and using HTTPS contributes to improved search rankings, enhancing visibility and trustworthiness.
- Cookie Security: HTTPS protects user cookies from interception, reducing the risk of session hijacking and enhancing overall session security.
- Compliance Requirements: Many modern web standards and security regulations mandate the use of HTTPS, ensuring alignment with industry best practices and legal requirements.
Incorporating HTTPS into your Laravel applications is not just a security measure; it’s a standard that fosters user trust and compliance with evolving web standards. This commitment to HTTPS aligns with the broader goal of creating resilient and trustworthy Laravel applications in the dynamic digital landscape.
2. Implement Authentication and Authorization
Robust authentication and authorization mechanisms are the backbone of safeguarding user access and data integrity. For Laravel applications, implementing these measures not only ensures the legitimacy of user interactions but also establishes granular control over resource access.
- User Authentication: Utilize Laravel’s built-in authentication system to verify user identities, requiring secure login credentials and enhancing overall account security.
- Role-Based Authorization: Implement role-based access control (RBAC) to define and manage user roles, ensuring that individuals have access only to the resources and functionalities essential to their tasks.
- Two-Factor Authentication (2FA): Enhance security by enabling 2FA, adding an additional layer of verification beyond passwords to fortify user accounts. For modern, passwordless authentication methods, explore Laravel Passkeys for a more secure and user-friendly login experience.
- Secure Password Policies: Enforce strong password policies, including complexity requirements and periodic password updates, to prevent unauthorized access through weak credentials.
- Audit Trail Logging: Implement comprehensive audit trail logging to track user actions, facilitating the detection of suspicious activities and providing a robust security trail.
The implementation of strong authentication and authorization measures in your Laravel applications is paramount for safeguarding user accounts and maintaining data integrity. Conducting these practices contributes to the creation of trustworthy and resilient Laravel applications in the ever-evolving landscape of web security.
3. Sanitize User Input
It is a critical practice to prevent various forms of attacks, such as SQL injection and cross-site scripting. By ensuring that user inputs are cleansed and validated, developers can fortify their applications against potential vulnerabilities.
- Use Laravel Validation Tools: Leverage Laravel’s built-in validation tools and request validation methods to streamline the validation process and enforce data integrity.
- Avoid Dynamic Queries: Refrain from constructing dynamic SQL queries using user input directly, opting instead for parameterized queries to prevent SQL injection attacks.
- Escape Output: Utilize Laravel’s Blade templating engine to automatically escape output, preventing cross-site scripting (XSS) vulnerabilities by rendering user-generated content safely.
- Content-Length Limitations: Enforce reasonable content-length limitations on user inputs to mitigate the risk of denial-of-service (DoS) attacks through resource exhaustion.
Prioritizing the sanitation of user input is a foundational step in securing Laravel applications. This commitment to meticulous input handling aligns with Laravel’s emphasis on security, contributing to the creation of resilient and trustworthy web applications.
4. Use CSRF Tokens
Cross-Site Request Forgery (CSRF) poses a significant threat, and employing CSRF tokens is a pivotal defense mechanism. By integrating and validating these tokens, developers can fortify their applications against unauthorized actions and enhance overall security.
- Built-in Laravel Protection: Utilize Laravel’s built-in protection by incorporating CSRF tokens into forms, ensuring that requests originate from legitimate sources.
- Token Verification Middleware: Implement a middleware to verify the presence and validity of CSRF tokens on sensitive routes, adding an extra layer of protection against unauthorized actions.
- Secure Token Storage: Store CSRF tokens securely, avoiding client-side storage and ensuring that tokens are not susceptible to theft or manipulation.
- Regenerate Tokens: Dynamically regenerate CSRF tokens after each request to prevent token reuse and add an additional layer of security against token-based attacks.
The utilization of CSRF tokens is a fundamental practice in defending Laravel applications against unauthorized actions. This practice aligns with Laravel’s dedication to security, contributing to the creation of resilient and trustworthy web applications.
5. Implement Rate Limiting
Using Laravel rate limit is a proactive strategy to mitigate the risk of abuse and potential denial-of-service (DoS) attacks. By controlling the frequency of requests, developers can enhance the resilience of their applications against malicious activities.
- Throttle Requests: Utilize Laravel’s rate limiting functionality to throttle the number of requests from a single user or IP address, preventing abuse and unauthorized access.
- Granular Rate Limits: Implement granular rate limits for different routes or functionalities based on their importance and susceptibility to abuse, allowing for tailored security measures.
- Exponential Backoff: Employ exponential backoff strategies to gradually increase response times for repeated requests, discouraging automated or brute-force attacks.
- Monitoring and Logging: Implement robust monitoring and logging mechanisms to track and analyze rate-limited events, facilitating the detection of suspicious activity.
- API Rate Limiting: If applicable, implement rate limits specifically for API endpoints to protect against abuse and ensure fair usage by legitimate consumers.
This commitment aligns with Laravel’s dedication to security, ensuring the creation of resilient and trustworthy web applications in the ever-evolving digital landscape.
6. Keep Laravel and Dependencies Up-to-Date
Maintaining the latest versions of Laravel and its dependencies is a cornerstone of effective security practices. Regular updates ensure that your application benefits from the latest security patches, bug fixes, and enhancements, reducing vulnerabilities and enhancing overall robustness.
- Frequent Laravel Updates: Stay current with Laravel’s official releases, promptly applying updates to access new features, bug fixes, and, most importantly, security patches.
- Dependency Monitoring: Regularly monitor and update third-party dependencies, libraries, and packages to address vulnerabilities and maintain compatibility with evolving security standards.
- Security Mailing Lists: Subscribe to Laravel’s security mailing list and relevant third-party libraries to receive immediate notifications about security vulnerabilities and updates.
- Automated Dependency Checks: Implement automated tools and services to perform regular checks for outdated or vulnerable dependencies, streamlining the update process.
- Test Updates in Staging: Before applying updates to a production environment, thoroughly test them in a staging environment to ensure compatibility and identify any potential issues.
Keeping Laravel and its dependencies up-to-date is a proactive measure that significantly contributes to the overall security of your application. It aligns with Laravel’s dedication to security, fostering the creation of web applications that prioritize the latest standards and best practices in the continually evolving digital landscape.
7. Use Secure Coding Practices
By adhering to best practices and guidelines during the development process, developers can proactively mitigate potential vulnerabilities and build a resilient foundation for their applications.
- Avoid Hardcoding Secrets: Refrain from hardcoding sensitive information such as API keys, passwords, or cryptographic keys directly in the code, opting for secure storage solutions.
- Error Handling: Develop robust error handling mechanisms that provide meaningful feedback to developers without exposing sensitive information, reducing the risk of information disclosure.
- Session Security: Ensure secure session management, utilizing Laravel’s built-in features for sessions and cookies to prevent session hijacking or fixation.
- Regular Code Reviews: Conduct regular code reviews to identify and address security concerns, leveraging the collective expertise of the development team to enhance code quality.
The incorporation of secure coding practices is foundational for fortifying Laravel applications against potential security threats. Conducting secure coding practices aids Laravel’s dedication to security, fostering the creation of web applications that prioritize resilience and trustworthiness in the ever-evolving digital landscape.
8. Cloud Security
Securing Laravel in cloud environments is crucial because deployment settings can create vulnerabilities if not managed properly. Whether you host on AWS, Azure, or DigitalOcean, hardening your servers and configurations protects your applications from attacks.
- Server Hardening: Configure firewalls, disable unnecessary services, and apply security patches to your cloud instances.
- Secure Storage: Encrypt sensitive files and databases to prevent unauthorized access.
- Access Control: Utilize role-based permissions and adhere to best practices for strong Laravel authentication across all cloud accounts.
- Monitoring: Track logs and unusual activity to detect potential threats early.
By focusing on cloud security, you ensure that your Laravel applications remain protected not only at the code and database levels, but also beyond them.
9. Securing Laravel Apps in CI/CD Pipelines
Security in the development pipeline is a proactive way to prevent vulnerabilities from reaching production. Integrating checks into CI/CD ensures safe and reliable deployments.
- Automated Scanning: Run vulnerability scans on code, dependencies, and container images during the build process.
- Testing Before Deployment: Enforce automated tests to catch security issues before production release.
- Verified Builds Only: Deploy only builds that pass security checks to reduce the risk of introducing vulnerabilities.
- Monitoring Pipeline: Keep an eye on pipeline logs and alerts for unusual activity or failed checks.
By embedding security in CI/CD, you reduce risks early and maintain consistent protection throughout your Laravel application lifecycle.
For specific security errors or to enhance overall security, consider quick assistance from a Laravel development company. It expedites issue resolution and ensures a secure web environment.
How to Handle Security Vulnerabilities in Laravel?
In the ever-evolving landscape of maintaining flawless web security, addressing vulnerabilities is a critical aspect of maintaining the integrity of Laravel applications. By adopting a proactive and comprehensive approach, you can effectively identify, mitigate, and respond to potential security threats, ensuring the continued trustworthiness of your web applications.
1. Promptly Apply Security Updates
The timely application of security updates is a foundational practice to safeguard against emerging threats and vulnerabilities. Keeping your Laravel framework and associated dependencies up-to-date is a proactive measure that significantly contributes to the overall resilience of your web application.
- Monitor Laravel Security Advisories: Stay vigilant about Laravel security advisories to promptly receive information about identified vulnerabilities and recommended updates.
- Regularly Update Dependencies: Ensure that third-party libraries and packages used in your Laravel project are regularly updated to incorporate the latest security patches.
- Automated Update Checks: Implement automated tools or services that regularly check for available updates, streamlining the process and minimizing the risk of overlooking critical security patches.
Prioritizing the swift application of security updates forms the bedrock of a resilient Laravel application. By consistently fortifying your web application against potential vulnerabilities, you contribute to the creation of a robust and trustworthy digital presence.
2. Implement a Responsible Disclosure Policy
Safeguarding your Laravel application involves more than just technical measures; establishing a responsible disclosure policy is a key component of an effective security strategy. By creating an environment that encourages the responsible reporting of vulnerabilities, you enhance collaboration and expedite the resolution of potential threats.
- Accessible Reporting Channel: Establish a clear and accessible channel for security researchers and users to report vulnerabilities responsibly, fostering a cooperative approach to security.
- Prompt Acknowledgment and Response: Ensure prompt acknowledgment and response to reported vulnerabilities, demonstrating a commitment to swift issue resolution and maintaining transparency.
- Collaborative Resolution: Engage collaboratively with the reporting party to address and resolve the reported vulnerabilities, leveraging the expertise of both internal and external stakeholders.
Embracing a responsible disclosure policy underscores your commitment to transparency and collaborative security efforts in the realm of Laravel applications. This proactive approach not only aligns with Laravel’s dedication to security but also contributes to the creation of a trustworthy and resilient web presence in today’s dynamic cybersecurity landscape.
3. Conduct Regular Security Audits and Educate Users
Regular security audits help identify and fix vulnerabilities before they can be exploited. By integrating systematic assessments into your development process, you strengthen your Laravel application against evolving threats.
- Routine Code Reviews: Regularly review your code to identify and address potential security issues.
- Penetration Testing: Simulate real-world attacks to reveal hidden vulnerabilities.
- Dependency Scanning: Keep third-party libraries up-to-date and secure.
- User Education: Inform your team and users about security best practices to create a culture of vigilance.
Combining regular audits with user awareness ensures a proactive defense, keeping your application resilient and your users protected.
4. Implement Web Application Firewalls (WAFs)
Safeguarding your Laravel application goes beyond code-level defenses; implementing Web Application Firewalls (WAFs) adds an additional layer of protection. By scrutinizing and filtering HTTP traffic, WAFs serve as a proactive barrier against various web application attacks.
- Traffic Filtering: WAFs analyze and filter incoming HTTP traffic, blocking malicious requests and preventing common web application attacks such as SQL injection and cross-site scripting (XSS).
- Rule Customization: Customize WAF rules to align with the specific security requirements of your Laravel application, tailoring protection against emerging threats and vulnerabilities.
- Anomaly Detection: Leverage WAFs for anomaly detection, allowing the identification of unusual patterns or behaviors in web traffic, which may indicate potential security threats.
The integration of Web Application Firewalls (WAFs) into your Laravel security strategy reinforces your application’s defenses against a myriad of web-based attacks. With traffic filtering, rule customization, and anomaly detection capabilities, WAFs offer a robust shield against evolving security threats.
Let’s Summarize
Securing a Laravel application is very important. The risks are real, and attackers are always seeking vulnerable points. By following best practices such as using HTTPS, keeping your framework up to date, and validating user inputs, you make your applications safer for both your users and your business.
Laravel provides powerful tools to help with security. The key is to use them carefully and consistently. Regular checks, Laravel secure coding habits, and a proactive approach will help keep your projects protected.
Security is about trust. When users know their data is safe, it strengthens your reputation and makes your applications more reliable. For strong, secure Laravel apps, hire dedicated Laravel developers. They can fix vulnerabilities and keep your application safe, allowing you to focus on growing your business.
FAQs on Laravel Security Best Practices
What is the security mechanism of Laravel?
Laravel provides built-in security mechanisms like CSRF protection, password hashing (Bcrypt/Argon2), input validation, SQL injection prevention, and XSS protection to secure applications.
Why should I regularly update Laravel and its dependencies for security purposes?
Regular updates patch known vulnerabilities, fix bugs, and ensure compatibility with latest security standards, keeping your Laravel app protected from emerging threats.
What is the default security in Laravel?
By default, Laravel offers CSRF protection, escaped output, secure password hashing, route protection via middleware, and form validation to enforce a secure development environment.
Build Powerful Laravel Applications
Learn how to leverage Laravel's powerful features for efficient and scalable web development.





